Forced Browsing vs. Command Injection: Why AppSec Training for Developers Matters
- Gyan Chawdhary, Head of Application Security, ThriveDX's Enterprise Division
The numbers are dire. Supply chain attacks double in 2021. Data breaches cost $4.24 million, on average. 483 Crypto.com wallets ransacked for $31 million.
We know that employees with low security awareness cause most cyber damage, but what about other attack vectors? And who should understand the difference between forced browsing vs. command injection attacks?
Web Application, API Attacks Up Sharply
Web application attacks comprise 26% of all breaches. Application-layer DDoS attacks are up 72% year over year.
As enterprises move more of their data, code and operations to the cloud, attacks against those assets are increasing dramatically. API attacks are up a stunning 686%.
Long story short, there are many more applications than trained developers to defend them.
In this post, we’ll examine some of the most common application vulnerabilities according to the Open Web Application Security Project (OWASP).
The OWASP Top 10 updates every three to four years and covers the top 10 application security risks.
Forced Browsing vs. Command Injection + 6 More AppSec Vulnerabilities
SQL Injection
SQL Injection is the OG of application layer attacks, and still packs a punch. This one vulnerability accounted for 8.1% of all data breaches in 2022.
SQL is a programming language allowing threat actors to “talk” to large databases using a language not unlike English.
SQL Injection can query, operate, and administer data systems. It can allow threat actors to authenticate without supplying a correct password.
Once in, users can read sensitive data from the back-end database, modify, or delete data and issue other commands.

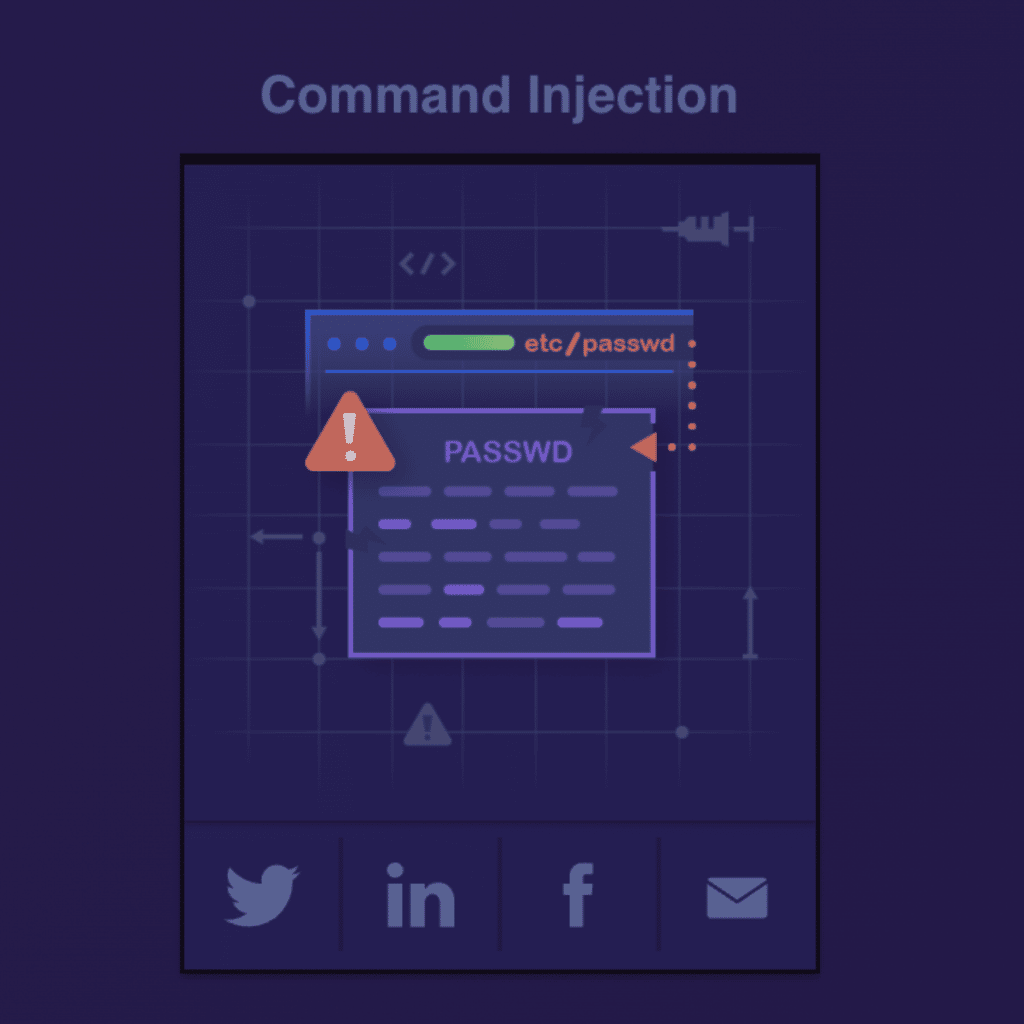
Command Injection
Command Injection, also called Shell Injection, is similar to a SQL injection. But instead of injecting into a SQL query, a threat actor injects a command into the OS. According to OWASP, Command Injection’s goal is to execute arbitrary commands on the host operating system via a vulnerable application.
Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. The attacker-supplied OS commands usually execute with the vulnerable application’s privileges.
In other words, Command Injection attacks inject OS commands. This allows hackers to compromise the entire application, take full control of the server – even attack other systems within the organization.
Forced Browsing
Not what it sounds like. Forced Browsing, also called Directory Enumeration, is a brute force attack technique to gain access to restricted pages or other sensitive resources in a web server. It does this by forcing or guessing the URL directly.
If the restricted URLs, scripts, or files lack appropriate authorization, these resources can be vulnerable to forced browsing attacks. This would hypothetically allow hackers to access restricted files and view sensitive information.
XML Entity Injection
XML External Entity (XXE) Injection is a web security vulnerability allowing an attacker to interfere with an application’s processing of XML data.
In other words, targeting applications that transmit data between browser and server in XML format. By intercepting and modifying the data, an attacker can exploit potentially dangerous features of standard XML libraries.
These would include the parsing and loading of external entities to gain access to the server’s filesystem or interaction with backend systems that the application has access to. Sometimes an attacker can escalate an XXE attack to perform server-side request forgery (SSRF) attacks.
Reflected Cross Site Scripting
Reflected Cross-site Scripting (XSS) is a client-side code injection vulnerability that allows malicious JavaScript payloads to be injected within a user-supplied input, reflecting back within the web server’s response and executed on the client-side by the victim’s web browser.
Since the entire attack completes in a single request and response, it is known as a Reflected Cross-site Scripting vulnerability.
Components with Known Vulnerabilities
Components with Known Vulnerabilities allow attackers to simply make use of automated scan tools or perform manual analysis of the application to identify and easily exploit security flaws within applications.
Because third party libraries and frameworks usually execute with full privileges, this attack becomes even more possible.
According to Siemba, famous Components with Known Vulnerabilities victims include:
- Equifax (a US credit bureau organization)- breach due to unpatched Apache Struts web framework CVE-2017-5638
- Mossack Fonesca (Panama Papers law firm) breach- unpatched version of Drupal CMS used
- Ubuntu forums breach – Unpatched Forumrunner add-on
Cross Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated.
CSRF attacks specifically target state-changing requests, not theft of data since the attacker has no way to see the response to the forged request.
According to Imperva this attack can be particularly devastating, resulting in unauthorized fund transfers, damaged client relationships and lost passwords.
Clickjacking
Clickjacking is a technique used by threat actors to “steal clicks” by tricking users into clicking on malicious links. This class of attacks overlays a legitimate decoy user interface over a hidden application.
In other words, users might think they’re on a real Wells Fargo site but in effect they’ve landed on a dangerous lookalike site that’s very much not Wells Fargo.
Before figuring this out, they’re tricked into clicking a button or link in the UI they see, performing an unwanted action in the hidden application.
The most common clickjacking attack uses invisible iframes and prevention is often based on restricting the framing capability for websites.
Forced Browsing vs. Command Injection: Devs Must Know the Difference
With the migration of systems, software, and apps to the cloud, devs who can properly integrate security into their coding have never been more in demand.
Who else would understand the bigger threat: Forced Browsing vs. Command Injection? XML Entity Injection or Reflected Cross Site Scripting?
Unlike other AppSec programs, Application Security Training by ThriveDX (formerly Kontra) abounds with challenging yet teachable real-life scenarios that will integrate security best practices into your code from the bottom-up.
For more information on ThriveDX enterprise security training programs, please visit us at https://thrivedx.com/for-enterprise.

Gyan Chawdhary is a world renowned Application Security and Development expert. After previously founding Codebashing, which was acquired by Checkmarx in 2018, Gyan shifted focus to inventing a new disruptive technology to successfully train developers in cybersecurity and apply it in their code, this is how his latest company Kontra was formed. In 2022, Kontra was acquired by ThriveDX’s Enterprise Division and Gyan remains on as an Advisor with the company. Some of Gyan’s former customers include the New York Stock Exchange, FitBit and Microsoft.
Protect Your Organization from Phishing
Explore More Resources
- Article, News
- Article, News
- Article, News
- Article, Blog
Your Trusted Source for Cyber Education
Sign up for ThriveDX's quarterly newsletter to receive information on the latest cybersecurity trends, expert takes, security news, and free resources.

