8 Mobile Cybersecurity Threats You Should Take Seriously
- Cayley Wetzig, Head of Marketing Communications
Living in today’s digital society means that keeping private information and data security should be a top priority for both companies and individuals alike.
And with the growth in the capabilities of mobile devices, cybersecurity is no longer just a concern for corporations looking to protect their infrastructure.
In a 2022 Mobile Threat Study, 66% of organizations surveyed stated they have active BYOD programs in place, with 11% looking to implement the policy over the next year.
10% of the applications installed on the average BYO mobile endpoint are enterprise-focused, from multifactor authentication (MFA), data access tools, and communications.
42% of those in the study reported unauthorized apps & resources accessing enterprise data. Read more to learn how to protect against mobile cyber security threats.

Mobile Cybersecurity: Your Identity in Your Pocket
Mobile cybersecurity is more personal than you think; bear in mind that for most of us, our mobile devices hold a digital footprint that contains our entire identity.
From personal photos, contact lists, and banking information to emails and addresses, our devices hold a lot of personal data that fits together like a jigsaw puzzle to form an overall picture of our identity.
Should that data fall into the wrong hands, your identity could be replicated by a cybercriminal for financial gain at your expense.
Worse still, recovery can be next to impossible. Organizations can implement measures such as cybersecurity workforce training, but mobile devices are an unknown risk that often departs at the end of each day with the employee.
Mobile Cybersecurity: 8 Risks and Tips to Secure Your Devices
Tech companies are doing their best to create new defenses against cybersecurity, but the greatest protections come from being clued-up on mobile cybersecurity and knowing how to bolster your own defenses.
You should find ways to protect your data and information to reduce the risk of being victimized by scammers as far as possible. To that end, here are eight mobile cybersecurity tips that you can adopt into your day-to-day routine, keeping you safe against cyber threats.
1. Be Wary of Leaked Data
Leaked data is considered a top threat to enterprise security. What makes it especially infuriating is that it’s often not inherently malicious.
It’s more about users unknowingly making ill-advised decisions on which applications can view and transfer data and information.
TikTok, for example, has been widely criticized for the sheer amount of data that it collects from users. It has even become banned on some governmental devices.
One of the best methods that both corporate employees and individuals can use in the fight against data harvesting is to use a VPN (virtual private network) in day-to-day browsing.
A VPN obscures your IP address, while encrypting all of your data. As a result, it’s far harder for third parties to interrogate your connection and steal your data through man-in-the-middle or similar attacks.
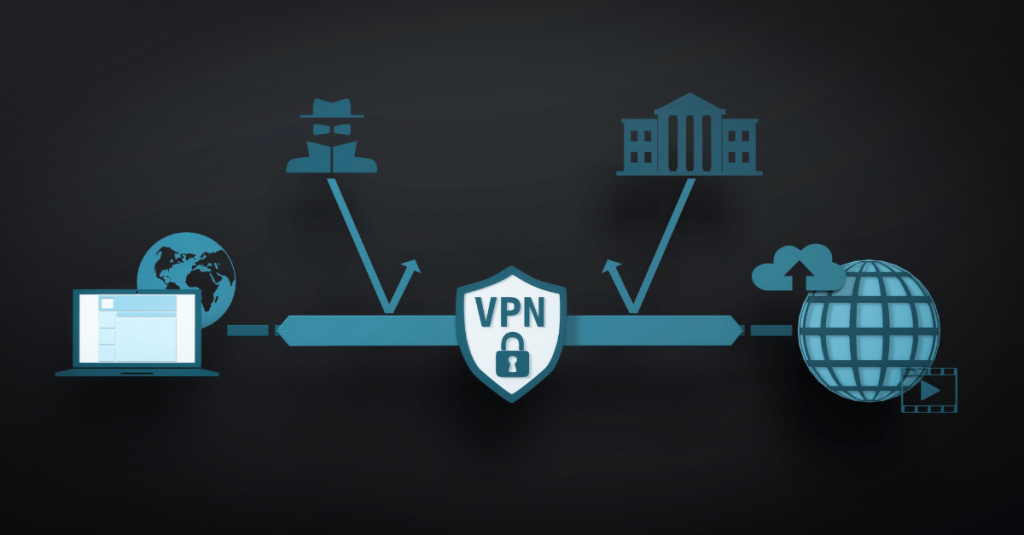
2. Avoid Unsecured Wi-Fi Networks
Remember that a mobile device is only as secure as the network it’s connected to. In an era where most people freely connect to public Wi-Fi networks while on the go, nearly a quarter of mobile users have connected to possibly unsecured and open Wi-Fi networks.
This is another use case for VPN software. Without a VPN, it leaves a lot of doors open on one’s perimeters.
However, choosing the right enterprise-class VPN is not that easy. VPN delivery should be more intuitive on mobile devices, offering the ability to choose which data is routed via the VPN , and which data may use your regular internet connection.
3. Beware of Phishing Attacks and Social Engineering Scams
A “Phishing Activity Trends Report for Q4 2021” from APWG found that phishing attacks reached an all-time high as 2021 came to a close.
Worse still, users are more likely to respond to a phishing attack on mobile devices than on a desktop, partly because a phone is where people most likely are to see a message first.
Our always-connected society is becoming more exposed to phishing than ever before, with new scams constantly surfacing. This includes an increasing number of phishing attacks and other social engineering scams that are beginning to arise in text messages, along with other social media services and games.
- Romance scams are rife on dating websites and social media platforms, with cybercriminals using fake profiles to snare victims. The FTC reported a $304m loss to romance scams in 2022.
- The “Friend in Need” scam, in which an unknown number messages somebody pretending to be a friend or family member who has lost their phone, has cost UK residents around £1.5m in the first half of 2022.
Social engineering scams can be more nefarious than regular phishing scams, because they prey on human emotions.
Cybercriminals spark up a connection with their victim, before leveraging that friendship or romantic connection to coerce a victim into lowering their defenses.
Using hardware-based authentication, whether through dedicated physical security keys such as the Titan of Google or through its on-device security key option for Androids, is deemed the most effective way to boost security and minimize the odds of a phishing-based takeover.
If you have a workforce to protect, then you should strongly consider cybersecurity awareness training.
Prospective victims can also safeguard themselves by:
- Not clicking on links in messages or emails from unknown senders
- Avoiding downloading any attachments within similar messages
- Implementing multi-factor authentication on all accounts and devices
- Not sharing any PIN code sent to them by a banking application
4. Keep Mobile Software Up to Date
Smartphones, tablets, and other smaller connected devices, known commonly as the Internet of Things (IoT), pose a new threat to enterprise security.
While traditional devices normally guarantee some degree of ongoing support from the manufacturer, IoT devices don’t generally come with guarantees of ongoing and timely software updates.
The risk here is that security vulnerabilities are constantly unsurfaced in new tech, and so the IoT is often the same as an open door.
If a vulnerability is discovered by a white hat hacker – or worse, by a cybercriminal – it may not be patched quickly, if at all.
- In 2022, Which? pointed out the simplicity of hacking a baby monitor
- In Summer 2022, Apple software was hacked due to security flaws
- In 2019, researchers successfully hacked an IoT-enabled fridge
Remember, while these interconnected devices offer convenience for everyday users at home, they also offer a convenient means to hack your home network if not properly secured or updated regularly.
Business owners should be wary, in our increasingly remote-working environment, to be wary of the devices that are given access to critical infrastructure and networking.
5. Enforce a Strict Password Policy
There are still mobile users that fail to properly secure their accounts. More than 20 million people use the password “123456,” and around half of all people use the same passwords across their personal and work accounts.
What’s more, only a quarter of American people are actively utilizing a password manager, which indicates that a large majority have no robust passwords in particular. Given the amount of personal – and since COVID-19, work – data stored on most people’s mobile devices, this is a disaster waiting to happen.
Individual internet users should consider a password manager as a priority. Such software not only safely stores your passwords behind a single, master password, but it can also choose a super-secure password for you.
Additionally, businesses should enforce password policies that require upper and lowercase alphanumeric characters and symbols, with a minimum specified password length. These policies prevent users from unintentionally creating weak points in your cyber security by using passwords that can be cracked in a fraction of a second.
6. Educate Yourself on Cryptojacking
We’ve mentioned how new threats are constantly emerging due to the expansion of mobile technology. Well, one such addition to the growing list of mobile threats list is cryptojacking.
This is an attack in which a third party exploits a victim’s device to mine cryptocurrency without the owner’s consent. The process can exploit organizations mobile devices for the financial gain of cybercriminals.
Cryptojacking poses a higher threat for Android device owners; Apple’s infamously stringent guidelines for modifying software or installing custom applications means that iPhones are relatively well-protected against this threat. So, consider using Apple hardware for organizational purposes.
Otherwise, Android users should steer clear of downloading APKs (custom application files) from third-party websites. While malicious apps filled with mobile ransomware and other malicious software can still make it into the Google Play store, using this official source is less likely to lead to a malware infection.
7. General Fraud via Mobile Apps
Mobile apps generate a large amount of revenue. Cybercriminals obviously follow the money; thus it’s not surprising that bad actors have found ways to pump cash from mobile ad revenue streams. The problem? Mobile ads can easily be a portal into a phishing scam.
Ad fraud can take various forms, but one of the most common is the use of malware for generating ad clicks.
In November 2018, a widely distributed botnet was shut down, which was using malware to control around 1.7 million computers across the globe. These victim devices were being used to fraudulently drive PPC traffic, generating around $29 million in fraudulent revenue.
Again, this comes down to having control over the software on your device. If using Android hardware, be wary of installing applications from third-party websites, or clicking on potentially malicious links.
8. Loss or Theft of Physical Devices
A device that’s lost or unattended can become a major risk in security, especially if it does not have a robust password or pin, and full data encryption.
Our mobile devices are often used as our second form of authentication for multi-factor authentication (MFA) too, so in a targeted attack, the loss of a device could result in identity theft or financial loss that affects all of your accounts.
Business organizations should not leave the responsibility in the user’s hands, because that is not enough.
Perhaps devices must remain on secured company premises, or perhaps business data should be disallowed from being stored on mobile devices. Regardless of your decisions, implement clear policies when it comes to device security.
If you’re concerned about other potential weak points in your cybersecurity strategy, consider employing outside organizations to pinpoint these flaws and suggest remedies.
Mobile Security Takeaways
The idea that mobile cyber security threats and risks are a myth is not true. With the mounting number of mobile devices used, the need for mobile security is gaining ground.
Now more than ever, it’s absolutely critical for users and manufacturers to ensure robust cybersecurity measures to minimize the threats that pose to our private information.
If we can impart you with some key tips that will immediately strengthen your mobile cybersecurity approach, consider this:
- Install a robust VPN software on your mobile device
- Use password manager software to create and store all passwords
- Enable multi-factor authentication on all of your accounts
- Do not use public Wi-Fi (without a VPN)
- Only install applications from official app stores, particularly on Android
- Update your devices as soon as new software becomes available
For organizations looking to educate their workforce on common cybersecurity threats, for both mobile and desktop, the best cybersecurity awareness training has proven to be a highly effective pathway.
Protect Your Organization from Phishing
Explore More Resources
- Article, News
- Article, News
- Article, News
- Article, Blog
Your Trusted Source for Cyber Education
Sign up for ThriveDX's quarterly newsletter to receive information on the latest cybersecurity trends, expert takes, security news, and free resources.

