OWASP Top 10 for Web
Empower your team with OWASP Top 10 and secure code training. Strengthen your web applications' defenses and minimize vulnerabilities effectively.
ThriveDX is now IronCircle » Learn More
Empower your team with OWASP Top 10 and secure code training. Strengthen your web applications' defenses and minimize vulnerabilities effectively.


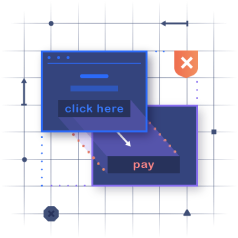

Code Injection is a general type of attack that injects code that is then interpreted or executed by the application, usually due to missing or insufficient input validation. Command Injection more specifically refers to the injection of operating system commands, which often allow attackers to compromise the whole application, take full control of the server, and even attack other systems within the organization.
Experience the full Kontra platform and see what it can do for you and your team.

Stay updated with news and press releases from ThriveDX
Are you ready to gain hands-on experience with the IT industry’s top tools, techniques, and technologies?
Take the first step and download the syllabus.
Contact (212) 448-4485 for more information. I also agree to the Terms of Use and Privacy Policy.
